<<< Hi Security>>>
The Raspberry Pi
is a credit card-sized computer that can crack Wi-Fi, clone key cards,
break into laptops, and even clone an existing Wi-Fi network to trick
users into connecting to the Pi instead. It can jam Wi-Fi for blocks,
track cell phones, listen in on police scanners, broadcast an FM radio
signal, and apparently even fly a goddamn missile into a helicopter.
The
key to this power is a massive community of developers and builders who
contribute thousands of builds for the Kali Linux and Raspberry Pi
platforms. For less than a tank of gas, a Raspberry Pi 3 buys you a low-cost, flexible cyberweapon.

With over 10 million units sold, the Raspberry Pi can be purchased in cash by anyone with $35 to spare. This makes it more difficult to determine who is behind an attack launched from a Raspberry Pi, as it could just as likely be a state-sponsored attack flying under the radar or a hyperactive teenager in high school coding class.
Thinking Like an Attacker
The Raspberry Pi has several unique characteristics that make it a powerful and easily accessible tool in a penetration tester's kit. In particular, the Pi is cheap and the components cost as little as a Lego set. Also, the Raspberry Pi is discreet; It's small, thin, and easy to hide. And thanks to running Kali Linux OS natively, it is flexible and able to run a broad range of hacking tools from badge cloners to Wi-Fi cracking scripts. By swapping the SD card and adding or removing components like a packet-injection capable wireless adapter, the Raspberry Pi can be customized to suit any situation.The Raspberry Pi on Offense
First,
it's important to manage your expectations and remain reasonable when
selecting a Raspberry Pi as a hacking platform. The Raspberry Pi is not a
super computer and doesn't have a tremendous amount of processing
power. It's not well-suited to processor intensive tasks like
brute-force WPA password cracking, or acting as a network attack as the
connection is too slow to fool users. That being said, the Raspberry Pi
is perfectly suited to many attack environments. We simply offload these
tasks to bigger computers and use the Pi as a data collector.
An active Raspberry Pi Wi-Fi jamming setup.
In my experience, the Raspberry Pi works exceptionally well
as a Wi-Fi attack platform. Due to its small size and large library of
Kali Linux-based attack tools, it's ideal for reconnaissance and
attacking Wi-Fi networks. Our offensive Kali Linux build will be geared
towards anonymous field auditing of wired and wireless networks.
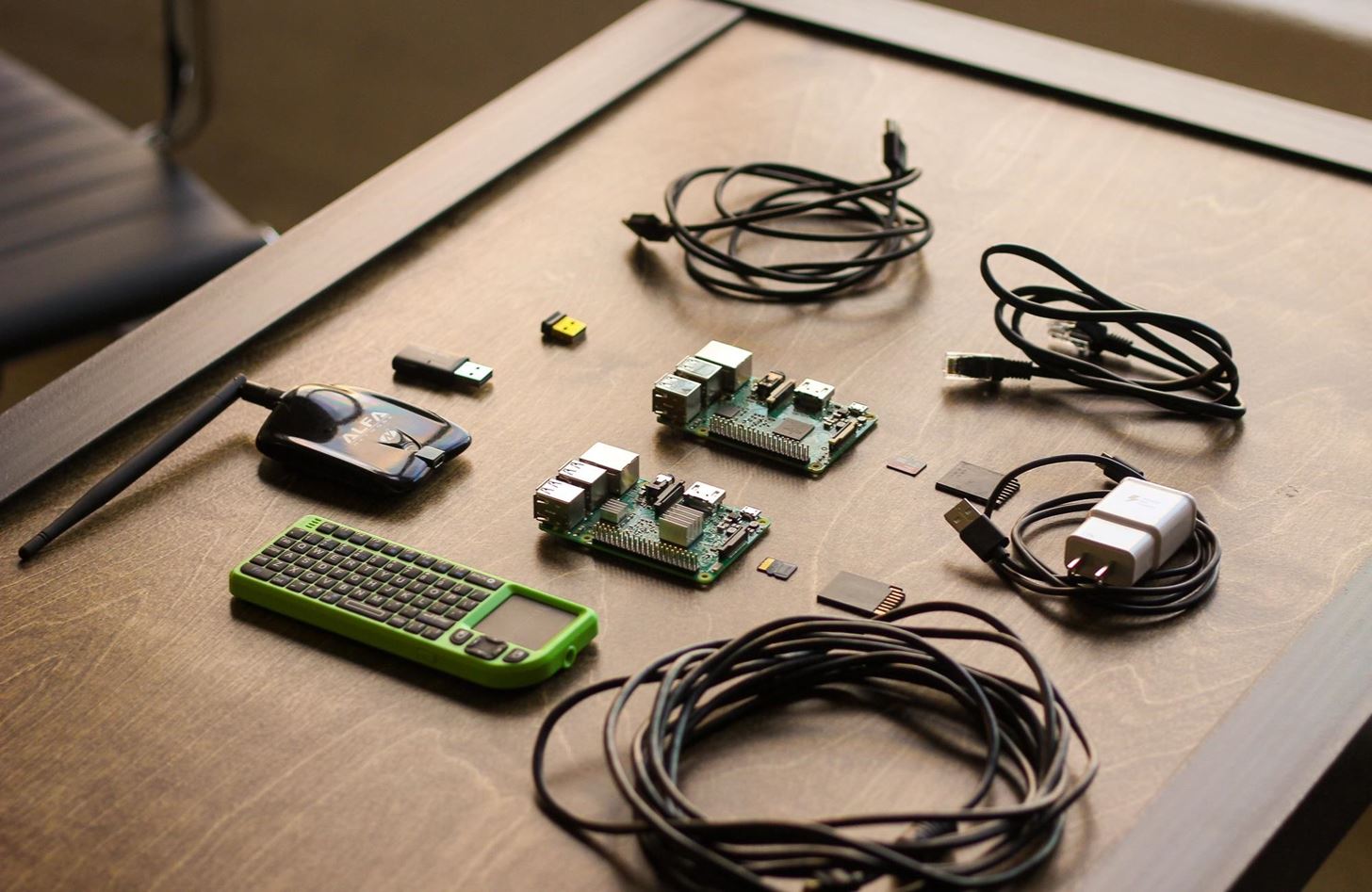
The Basic Components of Our Attack System
Here are the basic components needed to build our Pi attack system, and why we need them. If you're just starting out, this excellent Raspberry Pi Kit from CanaKit includes most of what you need to get your Pi set up.
- Raspberry Pi: The Raspberry Pi 3 is the platform of these builds, coordinating and controlling all other components. Its low power consumption and flexible capabilities allow it to serve as a platform for running Linux-based operating systems besides Kali.
Raspberry Pi 3.
- Command and control (C2) wireless card: The purpose of the C2 wireless card is to automatically connect the Pi to the command AP (access point) such as your phone hotspot or home network. This allows remote control of the Pi discreetly or from a great distance via SSH (Secure Shell) or VNC (Virtual Network Computing). Fortunately for us, the Raspberry Pi 3 has a Wi-Fi card internally, but a wireless network adapter can also be added to a Raspberry Pi 2.
- Wireless attack card:: Our attack wireless card will be a Kali Linux-compatible Wi-Fi adapter capable of packet injection. This will be our attack surface and can be a long-range, short-range, or directional antenna depending on attack requirements. You can find a great guide to choosing one here.
- OS build cards: The micro SD card hosts the OS and brain of the computer and can be precisely configured for any desired environment. By creating customized cards, it is possible to rapidly change the configuration and function of a Raspberry Pi by simply swapping the card and components.
- Computer: You will also need a computer to download the firmware to load onto the micro SD card.
- Power supply: The Raspberry Pi uses a standard Micro-USB power supply, and nearly any android phone charger or battery pack will work to power a Pi. This allows for a number of different battery configurations to suit long-endurance reconnaissance or continuiously powered operations.
My Raspberry Pi hacking kit
- Ethernet cable (optional): An Ethernet cable allows you to bypass wireless authentication by directly interfacing with local networks to which you have physical access. Specialized attacks like PoisonTap can also take advantage of ethernet interfaces to infiltrate computers.
- Bluetooth keyboard (optional): A Bluetooth keyboard is helpful for interfacing when you have an HDMI connection.
- Case (optional): Every Pi needs a case to protect it.
Build Considerations
In designing this tutorial, I considered two primary modes in which you would be operating the Raspberry Pi. In our open configuration, the Raspberry Pi is connected to a display via HDMI cord with inputs running through a wireless mouse and keyboard. In our tactical configuration, you will use a laptop or smartphone to access the Raspberry Pi remotely via SSH. By connecting the Pi to our phone's hotspot or a nearby friendly AP, we can access the Raspberry Pi while still being able to use cellular data in the field.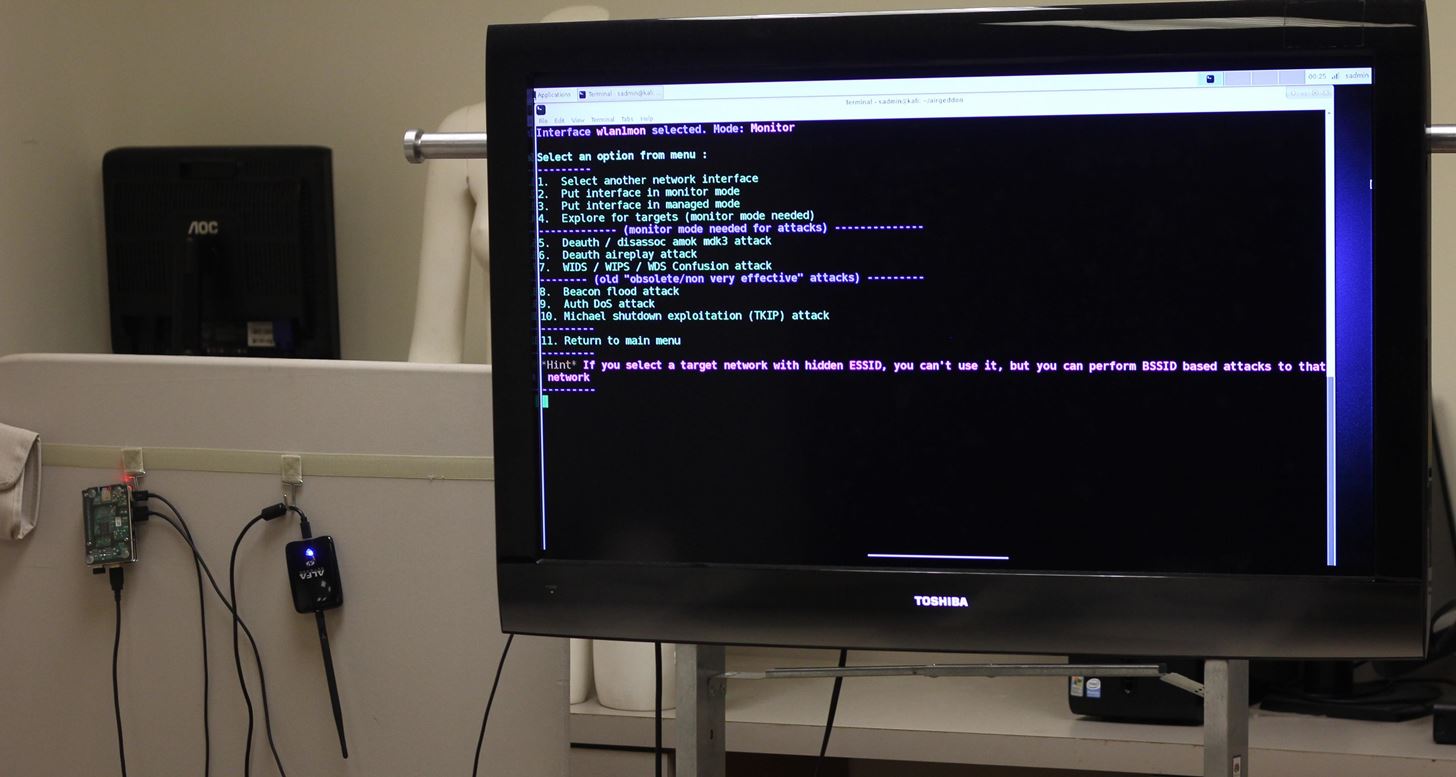
Lab configuration: Output over HDMI, input via Bluetooth keyboard. (Bottom) Tactical Configuration: Kali Linux via SSH.
How to Set Everything Up
In this guide, I'll show the steps needed to set up a Raspberry Pi 3 as a basic hacking platform with Kali Linux. I'll go over how to select a build to install, writing the disc image to a micro SD card, and the steps to run after first setting up your Pi. We'll update Kali Linux to the latest version to ensure everything works correctly, change the default SSH keys, and take care of some housekeeping like changing the admin password.As a note, there are many ways to configure Kali on a Raspberry Pi 3. Some include touchscreens, some are completely headless (accessed via network connections without a keyboard or display), and others use the internal Wi-Fi card to create a hotspot for remote control of the Pi. In selecting this build, I discounted any designs that included a power-hungry and fragile touchscreen or additional hardware, and settled a version optimized for our two different C2 scenarios.
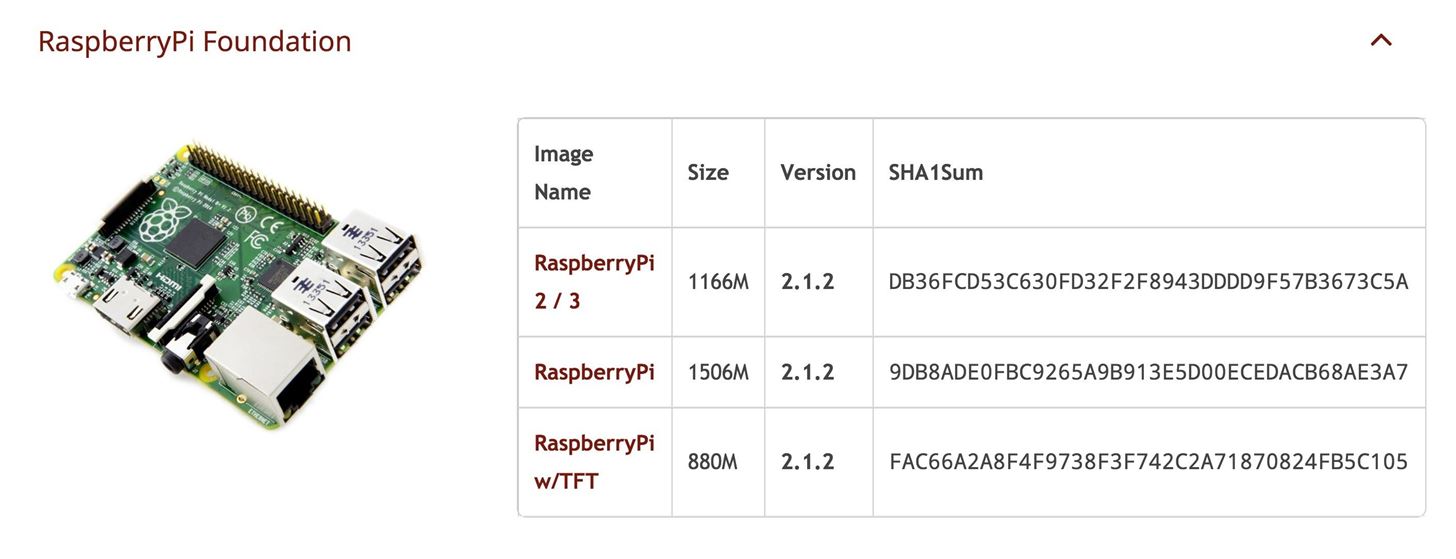
Download Kali Linux Image for the Raspberry Pi
Head to Offensive Security and download the latest Kali Linux image for the Raspberry Pi. As of this writing, it is "RaspberryPi 2 / 3" on version 2.1.2.Flash the Image to the Micro SD Card
You can use a tool like ApplePiBaker for Mac or Etcher to load your Kali image onto your SD card, but sometimes these can result in errors. To prevent that, we'll cover how to do this via Terminal on a Mac. If you use Windows, you can use Win32 Disk Imager to put your image on the card.On a Mac, before plugging in your SD card, run the following in Terminal:
df -hThis will display a list of all the disks attached to your system. Attach your SD card and run the command again, and note the filesystem name of your SD card (it's the one that wasn't there before). It should look like "/dev/disk2s1" and you should be very careful not to mix this up in the next steps, since doing so could overwrite your hard drive.









0 comments:
Post a Comment